Mobile and Web Application Security
Mobile and web application security is the new battlefront in the fight against hackers. We’ll help you test and secure your external facing assets to better protect your business online.
Mobile and web application security is the new battlefront in the fight against hackers. We’ll help you test and secure your external facing assets to better protect your business online.






Mobile and web applications are crucial to making data available to employees, customers and partners. But these systems that simplifydata availability within the business are attractive targets for cybercriminals.
These highly connected applications draw data numerous internal resources and databases. And if hackers can compromise your applications, they can use this foothold to exploit other network resources, or to steal IP and client data.
Identifying and addressing vulnerabilities in your web-enabled applications is essential to raising the standard of security within your operations.


Reduce attack potential
Identifying – and resolving – issues with your web applications and mobile apps will strengthen the overall security of your network. Reducing the number of available entry points will make your business much harder to attack.
Identify outdated APIs
Your web applications will use a series of APIs to link disparate services. Outdated APIs can be exploited to gain access to underlying data and credentials. Wavenet will analyse the APIs in use, advising where code updates are required to address these vulnerabilities.
Ascertain adherence to OWASP Top 10
Web and Mobile applications will be tested against the OWASP Top 10 methodology to ascertain adherence alongside using Wavenet's own internal methodologies.
Identify insecure services
Third party applications may connect to external data sets to provide additional functionality or context. Each of these services needs to be tested to confirm data is properly secured at every point.
Address unpatched apps, frameworks and mobile operating systems
Third party apps and software also need to be regularly updated to resolve potential exploits. Again, the Wavenet mobile and web application testing service will analyse all of your web-enabled assets and mobile apps to identify instances where updates are required.
Our security consultants will first inventory all of your applications. They will then research each, to obtain the latest threat intelligence for use in planning our security tests.
To better understand the severity of the problems identified, our consultants will carry out an extended series of tests. We will (harmlessly!) exploit each vulnerability to assess the degree of risk they present.
Using a combination of automated tools and our extensive knowledge of cybersecurity, we probe each of your applications for vulnerabilities. We’ll test for common exploits like SQL-injection and cross-site scripting (XSS), as well as more advanced vulnerabilities such as application logic flaws and session management flows.
Cybersecurity complicated – but the results of our tests don’t have to be. Our consultants will present the results of our web and mobile application tests in easy-to-understand reports. This ensure you can make informed strategic decisions more quickly and easily.
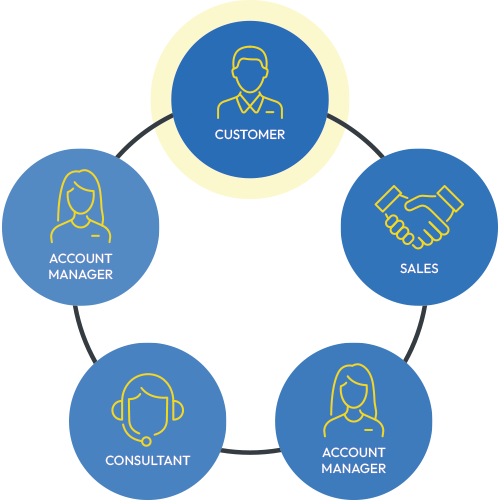
Other approaches we've witnessed have included convoluted steps and commonly ends with incorrect information being handed to the consultant assigned to the engagement.
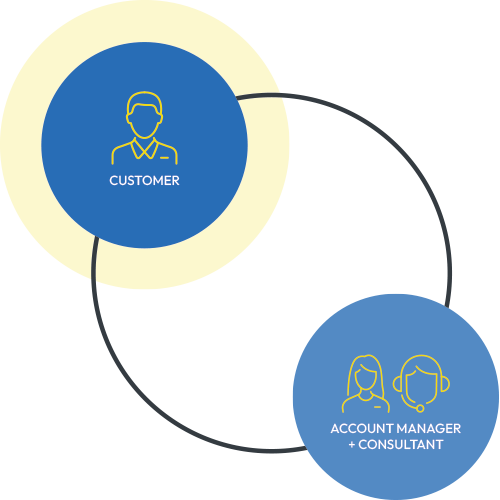 Our approach to security involves a qualified security consultant through the entire process to ensure quality, accuracy and consistency.
Our approach to security involves a qualified security consultant through the entire process to ensure quality, accuracy and consistency.




Every node on your network presents an attack surface for skilled cybercriminals. A penetration test targeted at your infrastructure helps reveal those vulnerabilities before they can be exploited.
More on Infrastructure Security
The only way to truly assess your IT security is to experience a cyberattack. Our Red Team Assessment uses real hacking tools and techniques to test your systems.
More on Red Team Assessment
With a PCI DSS assessment you can confirm payment data storage and transfer is fully compliant with the standard.
More on PCI DSS Assessment
How much damage could a lost smartphone do? The Stolen Device Assessment will help you know for sure.
More on Stolen Device Assessment
Would your security prevent an on-site attack? A Physical Security assessment will help you prepare for an unwanted visitor.
More on Physical Security Assessment
A GDPR assessment will confirm you have the relevant security safeguards in place to properly protect personal data against loss or theft – and a fine for breaking the law.
More on GDPR AssessmentOysta is very happy with the support, service and dedication of the Wavenet team. Working with the Oysta team every step of the way, not only did they check all security on the device, they also provided feedback on the quality of the hardware. I will be working with Wavenet again.
Mario Zuccaro, Founder and CEO, Oysta TechnologyWe have been really pleased with the service provided by Wavenet. We have found them to be extremely easy to work with. We also felt their fee structure was reasonable. We would recommend Wavenet to anyone looking for a PCI pen testing partner.
Andy Phillips, Inspired OutsourcingGreat service. Gave us exactly what we needed, as promised.
Philip Cunnington, TalkPlus NHSWe were extremely pleased with the service, knowledge and professionalism shown by Wavenet. After the remediation phase, we then ran a phishing exercise with them to remind staff of the need to be vigilant with external email communications. I would have no hesitation in using or recommending Wavenet in the future due to the quality of work carried out at a great price.
Graeme Thistlethwaite, ICT, Business Change and Business Support ManagerWavenet provided a high quality penetration service at a reasonable price … communications were great … the Pen test team flexed around us and our other commitments to get the job done. Thanks!
Darren Crombie, CEO, Upstream OutcomesGet all the latest news and insights straight to your inbox.
Just submit your details and we’ll be in touch shortly.